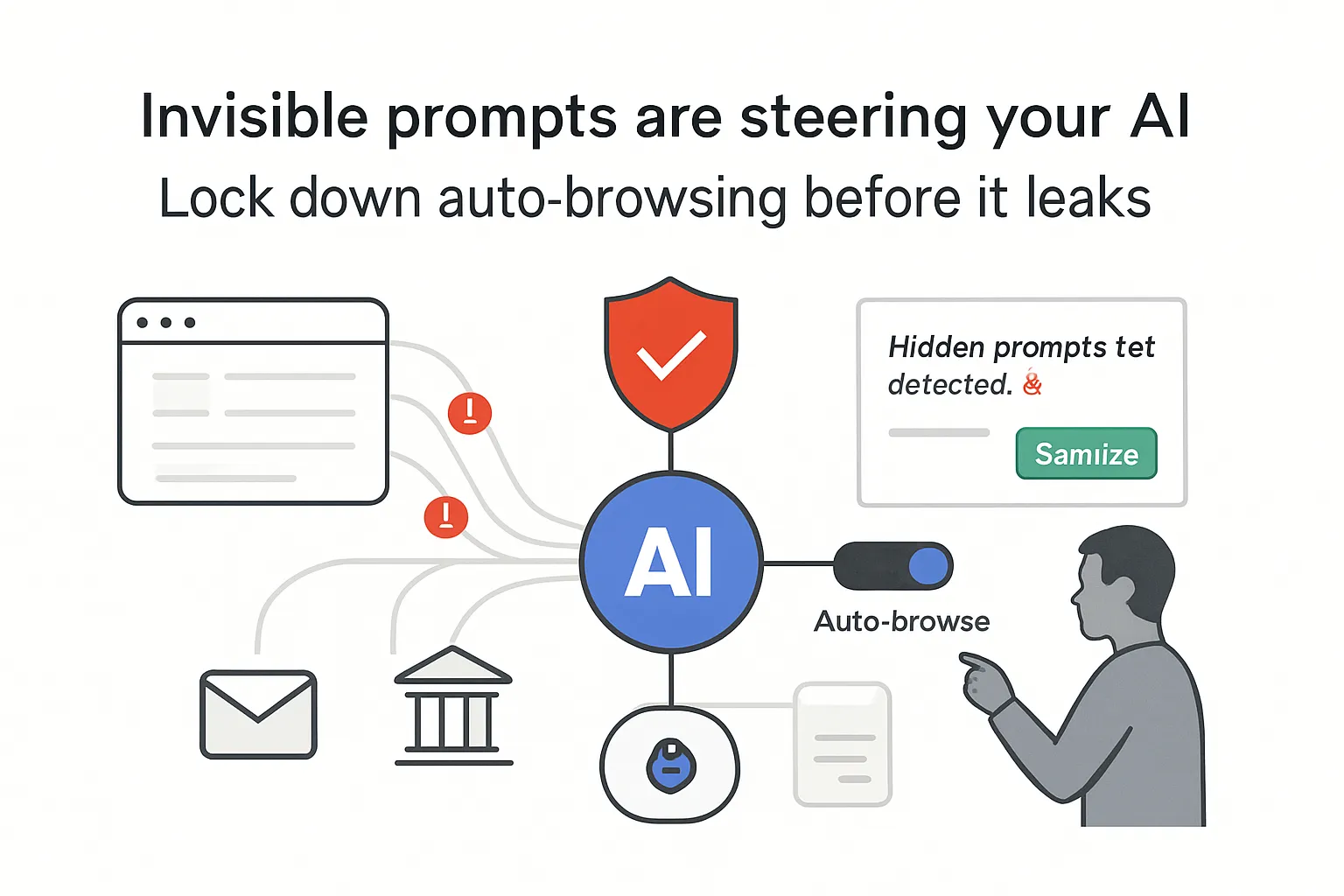
Brave has disclosed security vulnerabilities affecting AI-enabled web browsers, detailing how indirect prompt injection can hijack embedded assistants and trigger unintended actions. Technical details of the issues are available in the company's research post. The disclosure includes products such as Perplexity's Comet.

Key Details
- Brave documents methods for embedding hidden instructions in webpage content that assistants process as user commands, attributing the root cause to indirect prompt injection in agentic browsing flows.
- The report describes attacks against Perplexity Comet's screenshot workflow using low-contrast or near-invisible text. Brave says the assistant can extract that text and treat it as commands.
- Brave reproduced cases where webpage content overrode user intent during assistant-driven navigation. Similar behavior was observed in another AI browser, which Brave did not name.
- These assistants can act with the user's authenticated session across sites, potentially extending to email, banking, and workplace systems.
- Brave notified affected vendors before publication and is temporarily withholding details of an additional browser vulnerability.
Background
Brave characterizes the problem as systemic across AI browsers that accept and act on webpage content. Risks arise when assistants blend untrusted page data with trusted user prompts.
According to Brave, conventional same-origin policy protections do not constrain assistant actions performed on behalf of users. Natural language instructions embedded in webpages can trigger cross-domain activity, especially when agent features perform navigation, form submission, and data retrieval.



.svg)