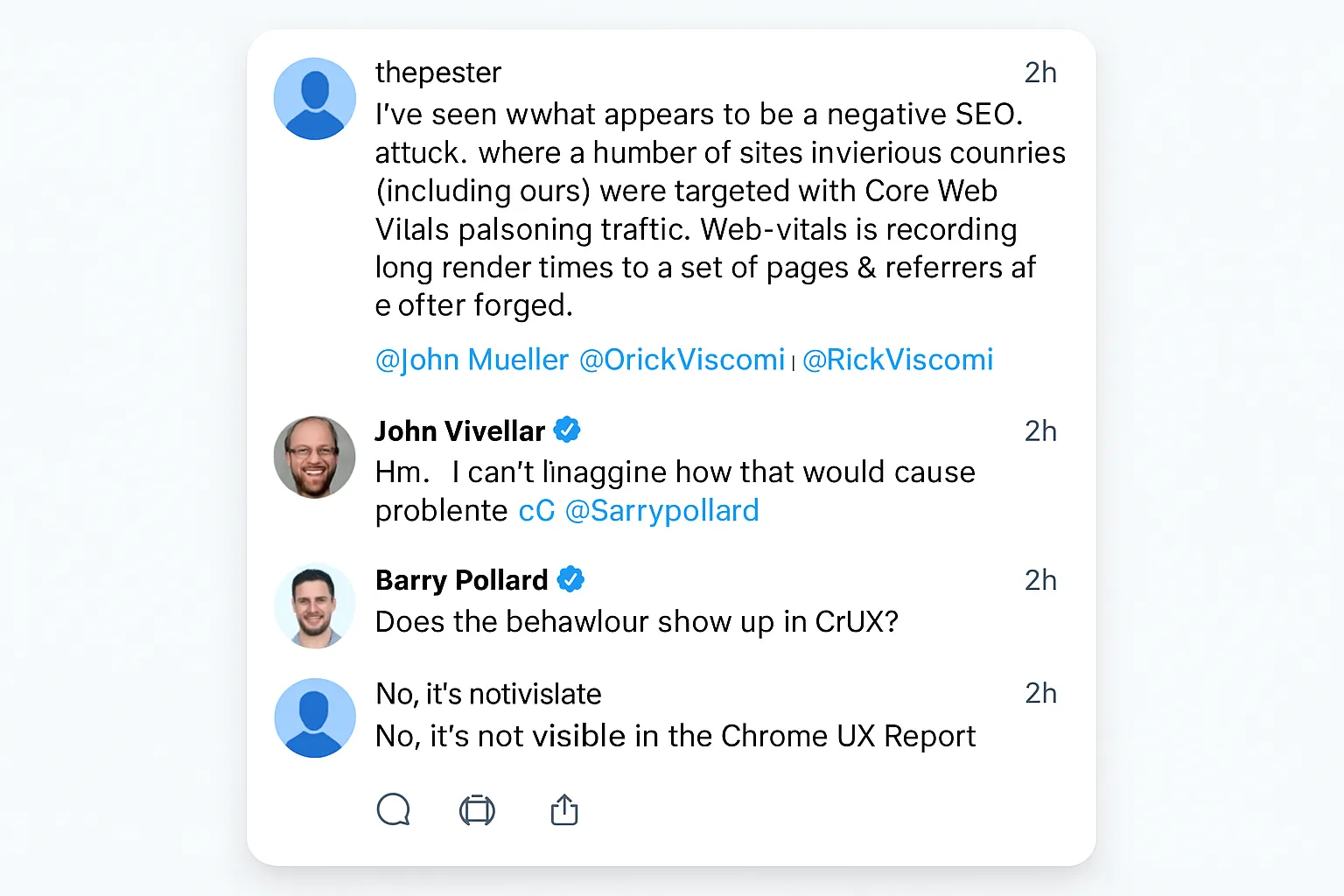
Google representatives addressed an allegation of Core Web Vitals "poisoning" in a public Bluesky thread, after a site using the web-vitals library recorded injected render delays. The exchange involved Google Search's John Mueller and Chrome Web Performance advocate Barry Pollard.
Key details
- A site operator posted a report describing a negative SEO attempt labeled Core Web Vitals "poisoning," citing intentional render delays observed across multiple sites and countries.
- According to the report, traffic targeted the same set of pages and often forged the referrer. Measurements were collected using the web-vitals JavaScript library.
- The poster tagged Google Search's John Mueller and Chrome's Rick Viscomi. Mueller responded and looped in Chrome Web Performance advocate Barry Pollard, saying he could not imagine the issue causing problems.
- Pollard asked whether the behavior appeared in the Chrome User Experience Report dataset. The poster said CrUX did not reflect similar problems.
- The poster also reported a cache-bypass denial-of-service incident affecting the site. Local web-vitals measurements captured degraded performance during the event.
Background
Core Web Vitals are user-centered performance metrics defined by Google. The current set includes Largest Contentful Paint, Cumulative Layout Shift, and Interaction to Next Paint. Google publishes metric definitions and thresholds.
The Chrome User Experience Report is a public dataset of anonymized field performance data from opted-in Chrome users. It aggregates data at the page and origin levels and is documented by Chrome Developers.
The web-vitals library enables real user monitoring on individual sites by sending metric values from visitors' browsers to analytics endpoints. The library is maintained by the Google Chrome team.
A denial-of-service attack floods a site with requests to degrade performance or exhaust resources. Cache-bypass variants send requests to the origin server rather than cached content.



.svg)