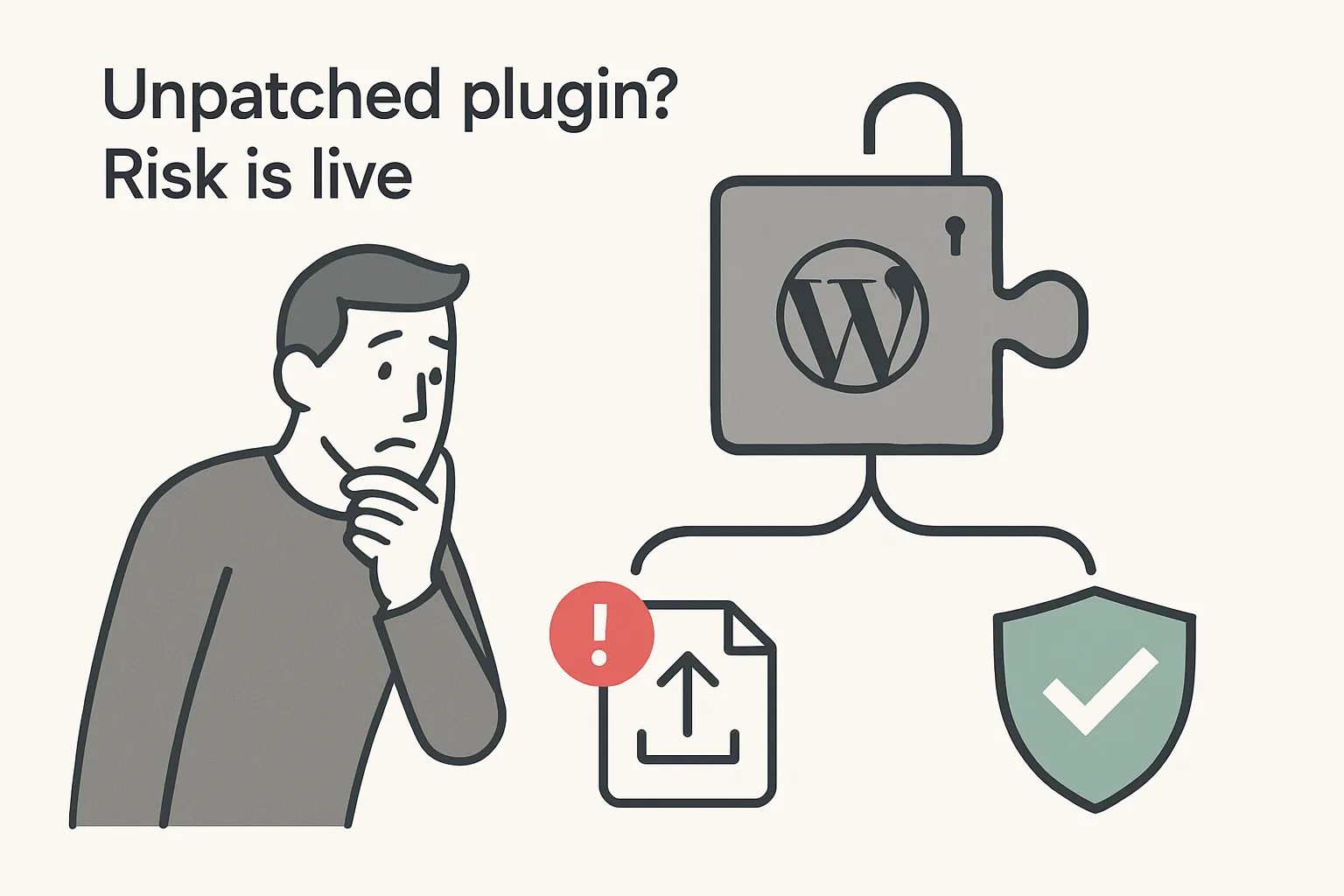
A high-severity security flaw in the AI Engine WordPress plugin exposed more than 100,000 websites to authenticated arbitrary file uploads. The issue, disclosed by Wordfence on 14 July 2025, affects versions 2.9.3 and 2.9.4. The developer released a patched build, version 2.9.5, the same day.
AI Engine WordPress Plugin Vulnerability
Wordfence assigned the flaw a CVSS 3.1 base score of 8.8. Any logged-in user with the low-privilege subscriber role can upload files of any type through the plugin’s REST API, potentially leading to remote code execution.
Key details
- Affected software: AI Engine plugin for WordPress
- Vulnerable releases: 2.9.3 and 2.9.4
- Active installations: about 100,000 (WordPress.org)
- Weakness category: authenticated arbitrary file upload
- Minimum required access: subscriber, if REST API is enabled
- Technical cause: missing MIME-type validation inside a REST API helper function
- Reported to vendor: 11 July 2025
- Public advisory: 14 July 2025
- Patch: version 2.9.5 adds strict file checks and URL-scheme validation
- CVSS score: 8.8 (high)
- Previous 2025 advisories: four earlier plugin flaws, three in July and one in June
- 2024 history: nine disclosed issues, including a 9.8-rated unauthenticated upload bug
Version 2.9.5 is now live in the WordPress plugin directory. Sites with automatic updates enabled received the fix within hours of publication.
Background Context
The AI Engine plugin integrates large-language-model features such as content generation and audio transcription. Its architecture relies on custom REST routes that accept media files and external URLs. When file-type checks are absent, attackers can upload executable PHP or shell scripts.
Subscriber-level exploits are particularly risky for membership, forum, and e-commerce sites that let visitors create basic accounts. Attackers can automate account creation and file upload in a single chain, bypassing moderating controls.
AI Engine’s latest disclosure is its fifth in 2025. The repeated incidents reflect a wider issue: Wordfence logged more than 4,000 plugin vulnerabilities across the WordPress ecosystem in 2024. Core mitigations such as the wp_check_filetype_and_ext function exist but rely on correct implementation by plugin authors.



.svg)