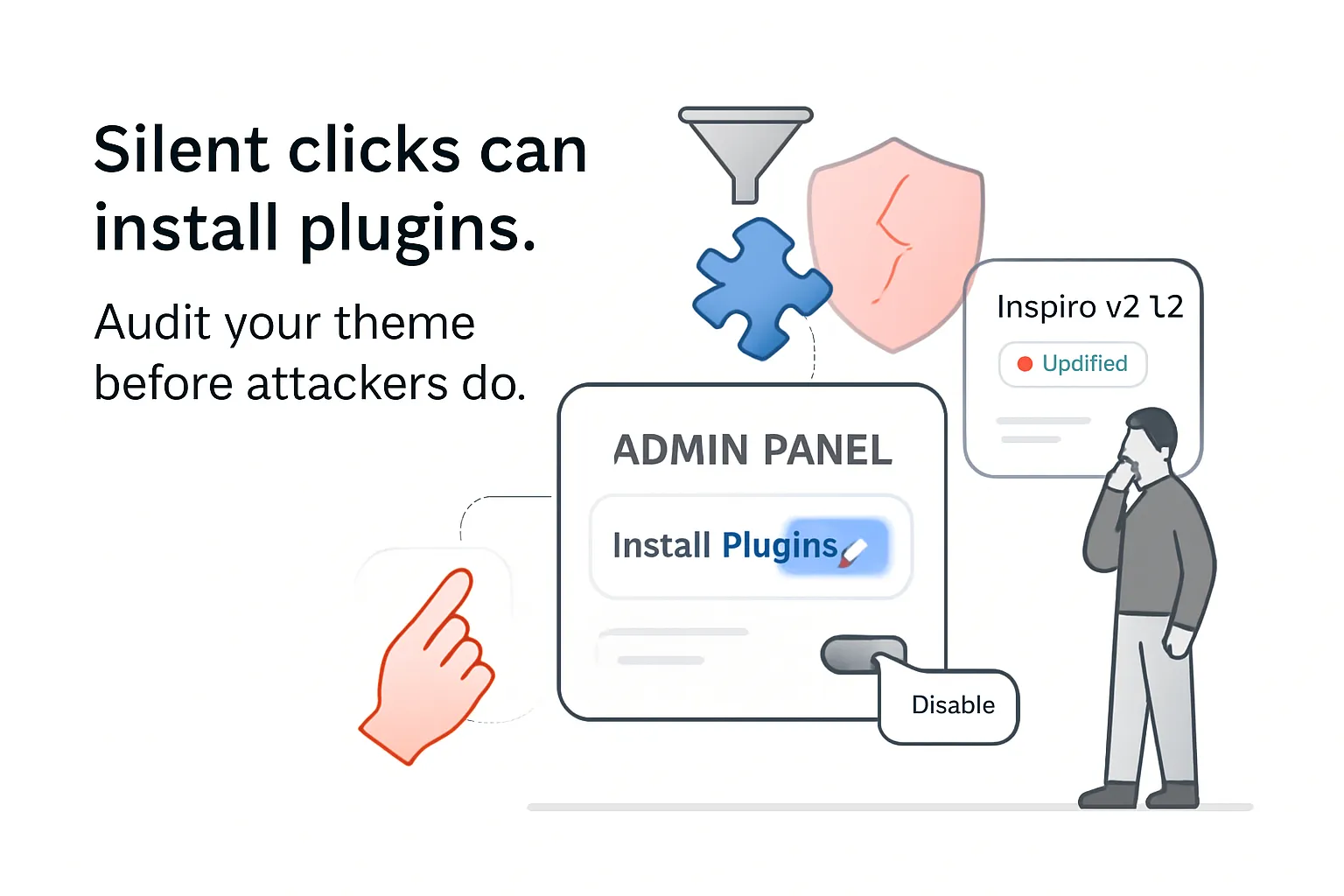
Wordfence disclosed a Cross-Site Request Forgery vulnerability in the Inspiro WordPress theme by WPZOOM that can enable arbitrary plugin installation via a forged request if an administrator is tricked into clicking a malicious link. The issue affects versions up to and including 2.1.2 and is rated CVSS 8.1 High, according to Wordfence's advisory.

Key details
- Product: Inspiro WordPress theme by WPZOOM
- Vulnerability: Cross-Site Request Forgery leading to arbitrary plugin installation from the WordPress repository
- Affected versions: Up to and including 2.1.2
- Severity: CVSS 8.1 - High
- Authentication: None required for the attacker; administrator interaction is required
- Cause: Missing or insufficient request validation
- Source: Wordfence threat intelligence advisory
"This makes it possible for unauthenticated attackers to install plugins from the repository via a forged request granted they can trick a site administrator into performing an action such as clicking on a link."
How the attack works
CSRF attacks exploit an authenticated user's browser to trigger unintended actions. On WordPress, an attacker typically needs to lure an administrator into clicking a crafted link or visiting a malicious page. If successful, the attack leverages the admin's existing session to perform actions such as installing plugins.
What site owners should do
- Check your site's Inspiro version. If it is 2.1.2 or earlier, treat it as vulnerable.
- Monitor the official theme listing for updates and apply any patch promptly: WordPress.org Inspiro theme listing.
- Avoid clicking untrusted links while logged in as an administrator.
- Limit administrator accounts to only those who need them and review recent administrative actions for any unexpected plugin installs.



.svg)