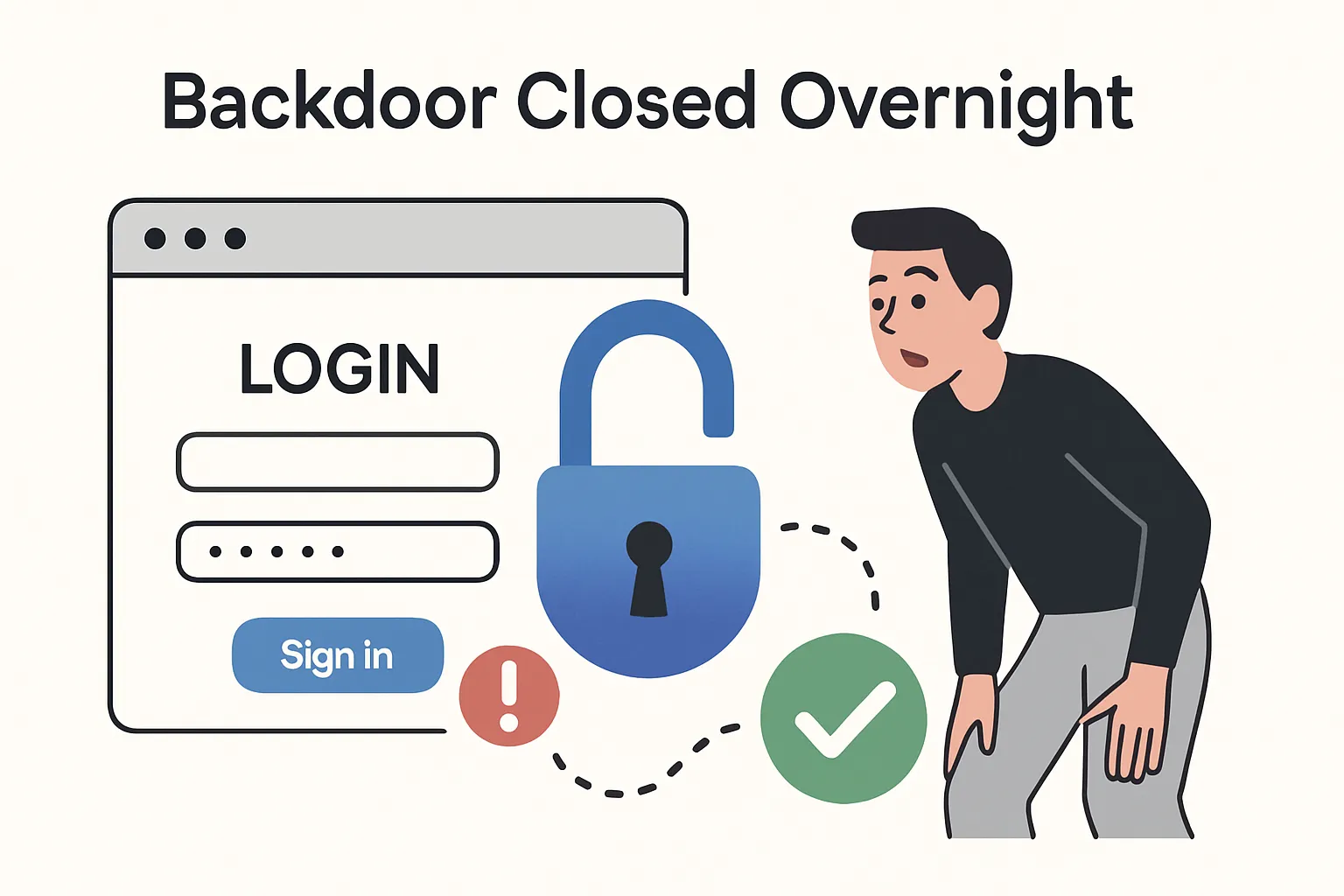
Cloud-security firm Wiz has disclosed a critical authentication flaw in Wix's Base44 low-code platform that could have allowed outsiders to access private enterprise applications. Wix deployed a fix within 24 hours of the report, and both companies say log reviews show no sign of exploitation.
How the flaw worked
Wiz researchers discovered that every Base44 application exposed a hard-coded application identifier ("app_id") in publicly accessible URLs and manifest files. With a valid app_id, an attacker could:
- Register a new user even when self-registration was disabled
- Receive a one-time password by email
- Complete the login process and bypass Single Sign-On controls
No elevated privileges or insider knowledge were needed, yet the flaw granted full access to internal tools for human resources, chatbots and knowledge bases that often store employee and customer personally identifiable information.
Remediation and timeline
Wiz notified Wix on 2 July 2024. Wix engineers immediately removed the exposed identifier and shut down the registration loophole the same day. Joint log reviews by Wiz and Wix have found no evidence of malicious activity.
"Wix continues to invest heavily in strengthening the security of all products and will keep monitoring for related issues," the company said in a statement.
Why it matters
Low-code platforms like Base44 speed up application development, but a single authentication gap at the platform layer can expose every app built on it. The incident underscores the need for rigorous security testing and continuous monitoring, even in no-code and low-code environments.



.svg)