Cloud security firm Wiz has disclosed a flaw in Wix Base44 Vibe that let attackers register rogue accounts and gain access to private enterprise applications. Wix deployed a patch within 24 hours, and no real-world exploitation has been confirmed.
Wix Vibe vulnerability
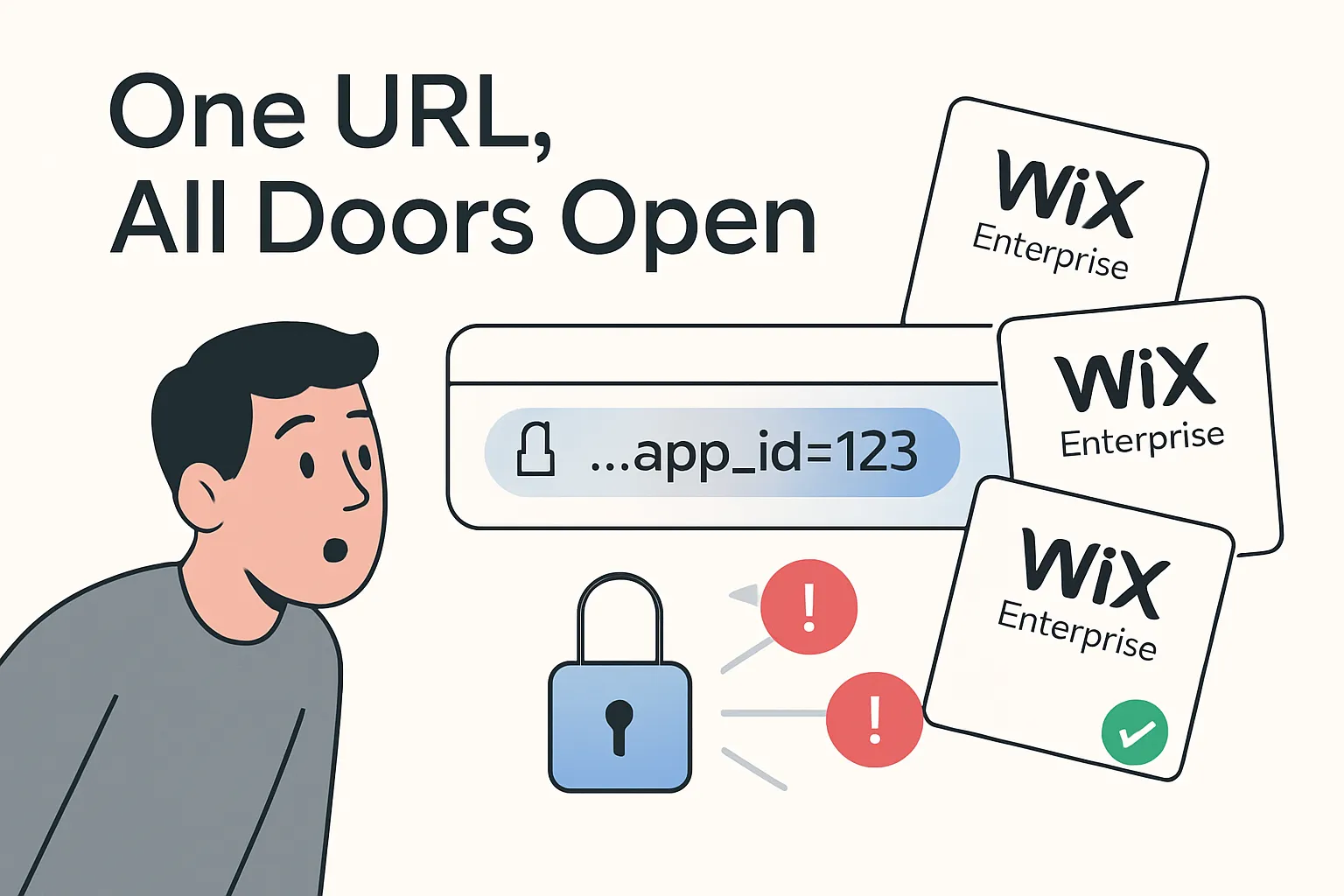
Researchers discovered that every Vibe app exposes its unique app_id in public URLs and in the manifest.json file. By copying that identifier, an attacker could initiate a registration request through the platform’s API even when sign-ups were disabled. Once the one-time password arrived by email, the new account could complete the single sign-on (SSO) flow and log in with full user privileges.
Key details and context
- The app_id appears in paths such as
/manifests/{app_id}/manifest.json, making it easy to harvest. - An attacker could send a POST request to
/api/v1/auth/signupwith the stolen value and any email address. - The system then emailed a one-time password that verified the account without rate limits.
- Logging in through SSO granted the same permissions as trusted staff accounts.
- Wix fixed the issue in less than a day after Wiz notified the company.
- Wiz has found no evidence of active exploitation.
Base44, launched by Wix in 2023, enables employees to build internal tools with minimal code. Wiz notes that fast low-code development can introduce security gaps when sensitive identifiers are left in public files.
Source citations
Wiz Research Uncovers Critical Vulnerability in AI Vibe Coding platform Base44 Allowing Unauthorized Access to Private Applications
Wix statement (via Wix.com)



.svg)