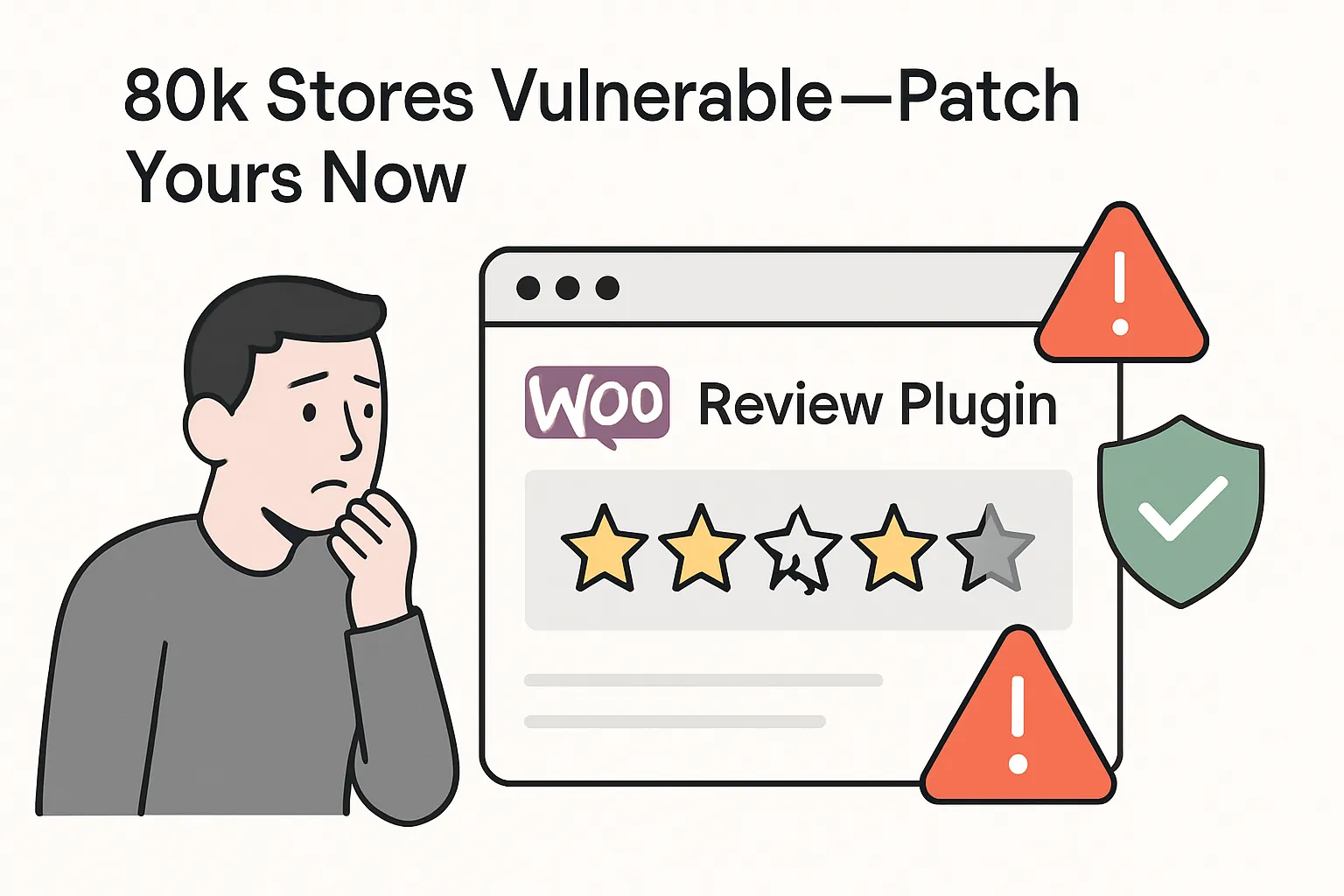
More than 80,000 WordPress sites using the Customer Reviews for WooCommerce plugin are exposed to a high-severity stored cross-site scripting (XSS) flaw disclosed by Wordfence on 23 July 2025. The vulnerability lets unauthenticated attackers inject malicious JavaScript into review pages. A patched version, 5.81.0, is already available in the WordPress repository.
Vulnerability Overview
The weakness affects every plugin release through 5.80.2. Attackers can abuse the unsanitised author parameter in a review submission to store executable code that runs whenever someone opens the compromised page. Wordfence rated the risk as high because exploitation does not require user authentication.
Key Details
- Disclosure date: 23 July 2025
- Impacted versions: Customer Reviews for WooCommerce 5.80.2 and earlier
- Attack vector: unsanitised author field in review forms
- Impact: stored XSS that executes in visitors’ browsers on page load
- Estimated installations affected: 80,000+ active sites
- Fixed release: 5.81.0 (published by developer Ivory Dev)
- Recommended action: update to 5.81.0 or later without delay
- Source: Wordfence advisory
Background
Customer Reviews for WooCommerce automates post-purchase emails and showcases user-generated content to increase trust in online stores. Its popularity widens the pool of potential targets whenever a flaw emerges. Stored XSS issues have plagued other WordPress extensions in recent years, making fast patch management critical for site owners.
Wordfence maintains a public vulnerability database and supplies virtual patches to its firewall customers. WordPress.org guidelines require plugin developers to sanitise user input and escape output, the two controls missing from the affected code path. Ivory Dev received Wordfence’s report and released the fix following standard responsible disclosure practice.



.svg)