Wordfence has disclosed a stored cross-site scripting (XSS) vulnerability in the Customer Reviews for WooCommerce plugin that could expose more than 80,000 WordPress stores to attack. The security firm published its advisory on 6 June 2024.
How the flaw works
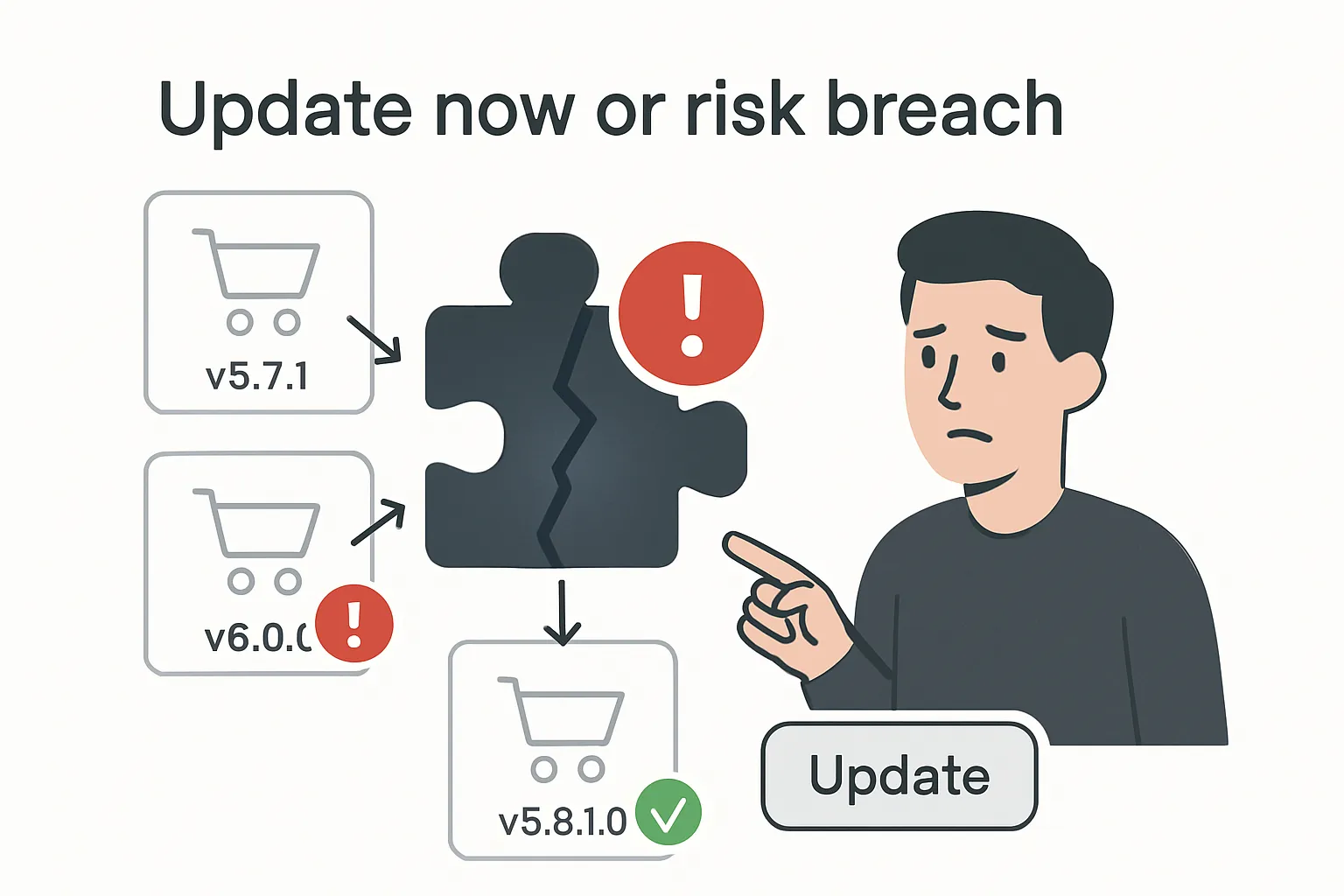
Versions up to 5.80.2 do not sanitize the "author" parameter or properly escape the value when it is rendered. An unauthenticated attacker can therefore inject malicious JavaScript that executes for every visitor who views the affected page, turning the XSS into a site-wide threat.
Key details at a glance
- Affected plugin: Customer Reviews for WooCommerce (≤ 5.80.2)
- Active installations: about 80,000 sites
- Attack vector: stored XSS, no login required
- Patched release: 5.81.0, issued by CusRev after Wordfence notification
- Disclosure date: 6 June 2024
Why it matters for store owners
The plugin is popular among WooCommerce merchants because it solicits post-purchase feedback and displays verified ratings that can boost sales. A successful XSS exploit could let an attacker steal customer data, redirect shoppers to malicious sites, or take administrative actions, undermining trust and revenue.
Recommended action
Site administrators should update to version 5.81.0 or later immediately. After patching, clear caches and review site logs for unusual activity to ensure no payloads remain in stored content.



.svg)