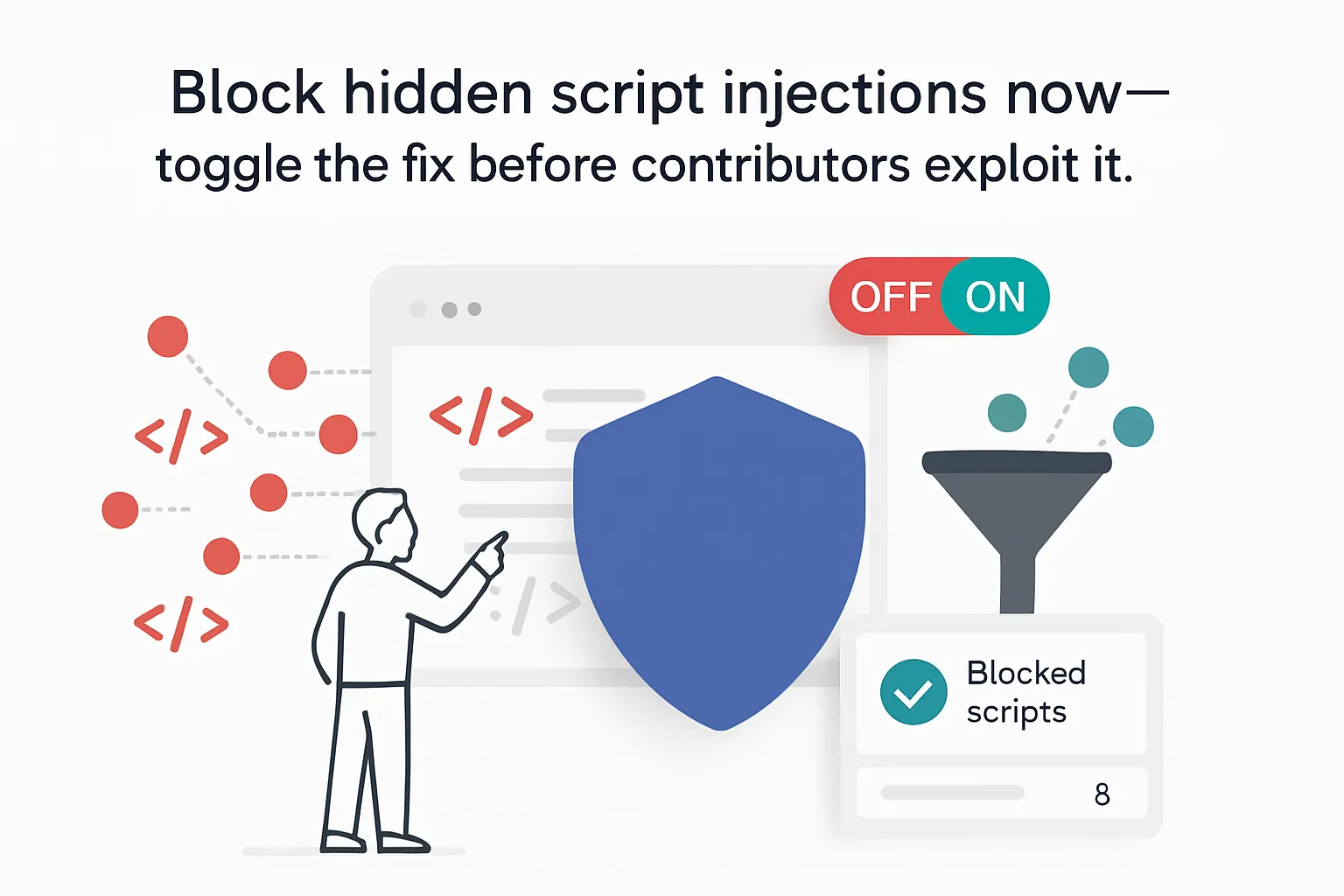
Wordfence has discovered and disclosed a stored cross-site scripting vulnerability in the WPBakery Page Builder plugin for WordPress. The issue affects versions up to 8.6.1 and requires contributor-level access to exploit. A fix is available in version 8.7.

WPBakery WordPress vulnerability
The flaw stems from insufficient input sanitization and output escaping in the plugin's Custom JS module. Authenticated users with contributor privileges or higher can inject arbitrary JavaScript into affected pages, which executes when a user views the compromised page.
- Plugin: WPBakery Page Builder for WordPress (slug js_composer)
- Vulnerability type: Stored cross-site scripting via Custom JS module
- Affected versions: Up to and including 8.6.1
- Fixed version: 8.7
- Required access: Authenticated contributor or higher
- Source: Wordfence advisory
Background context
WPBakery Page Builder is a drag-and-drop page builder frequently bundled with premium WordPress themes under developer licenses. Stored cross-site scripting vulnerabilities allow persistent script execution in site visitors' browsers when they load a page containing the injected payload. The identified vulnerable component is the Custom JS module.
Mitigation
- Update WPBakery Page Builder to version 8.7 as soon as possible.
- Review pages and any use of the Custom JS module for unexpected or unauthorized code.
- Limit contributor permissions where possible and monitor recent changes until the update is applied.
Source
Wordfence advisory - WPBakery Page Builder 8.6.1 stored cross-site scripting via Custom JS module



.svg)