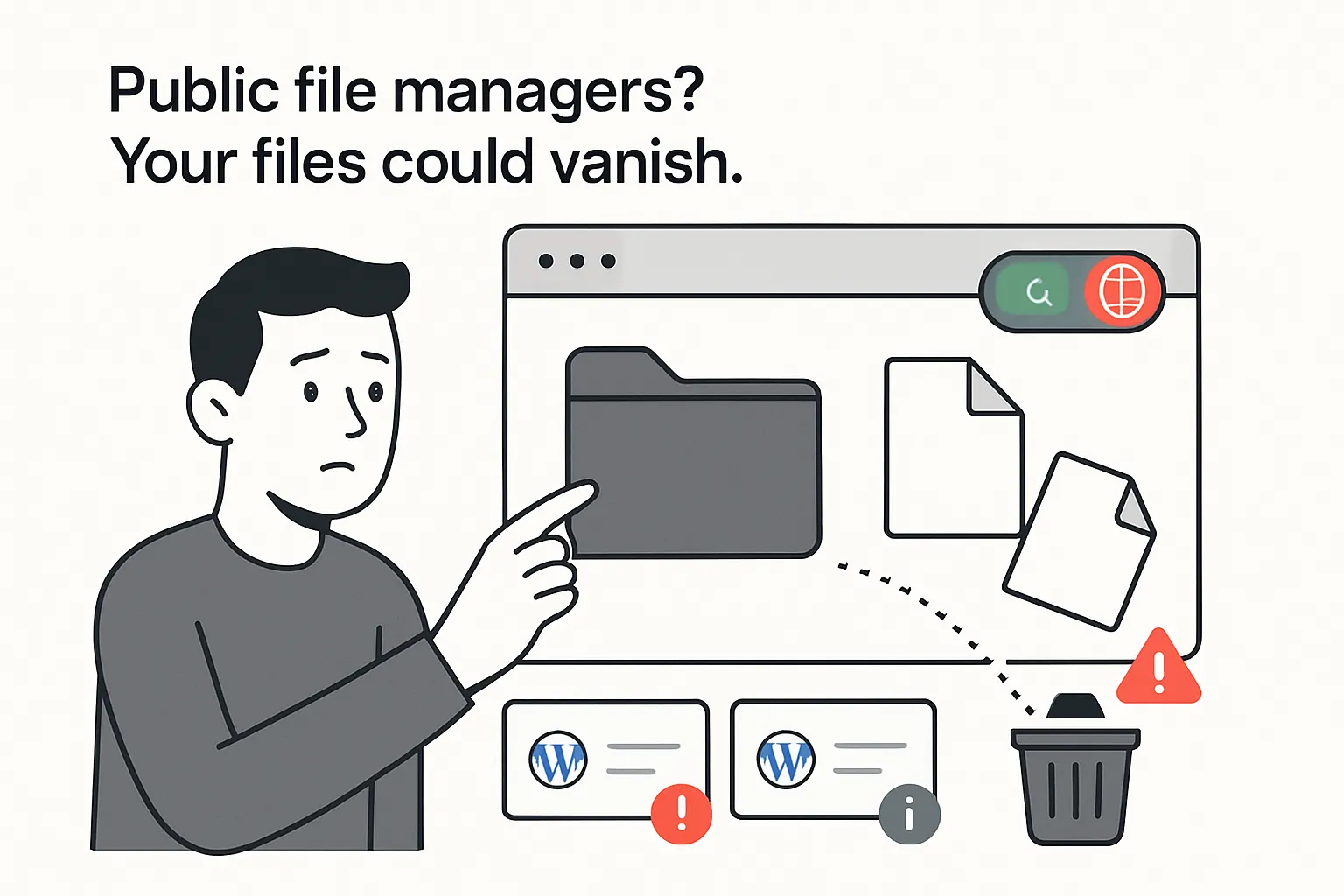
Wordfence disclosed a directory traversal flaw in the elFinder component used by three WordPress file manager plugins. The bug enables arbitrary file deletion and may affect up to 1.3 million sites, according to the Wordfence advisory. Unauthenticated exploitation is possible only if a site exposes the file manager interface publicly.

Key details
- The issue is a directory traversal to arbitrary file deletion vulnerability in elFinder versions 2.1.64 and earlier embedded by affected plugins.
- Attackers can manipulate file paths to escape allowed directories and delete files outside permitted folders.
- Unauthenticated exploitation is possible only when a site publicly exposes the file manager endpoint.
- Affected plugins named by Wordfence: File Manager, Advanced File Manager, and Filester - File Manager Pro.
- These plugins collectively account for up to 1.3 million installations, per the Wordfence advisory.
Background
ElFinder is a third-party file manager library integrated by several WordPress file management plugins. Versions 2.1.64 and earlier contain a directory traversal flaw that allows path manipulation using traversal sequences to reach files outside the intended directory. Wordfence, which operates a public vulnerability database, identified the vulnerable elFinder versions within the three plugins and outlined exploitation conditions. For project details, see the elFinder project repository.
What site owners can do
- Check whether your site uses File Manager, Advanced File Manager, or Filester - File Manager Pro.
- Ensure the file manager interface is not publicly accessible and is restricted to authenticated admin users.
- Follow guidance in the Wordfence advisory and apply any available plugin updates that address the embedded elFinder versions.



.svg)