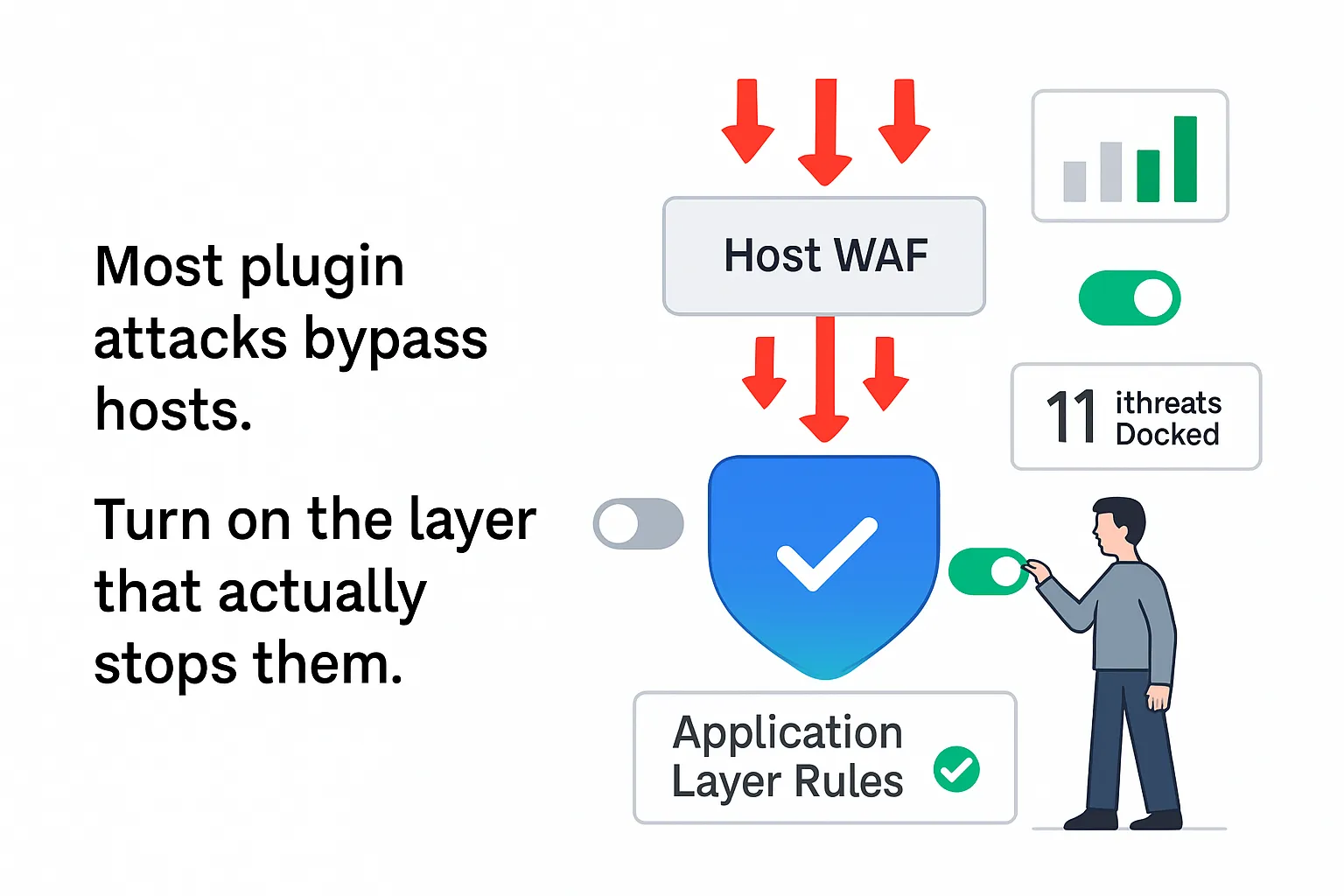
WordPress plugin and theme exploits bypassed 87.8% of host-layer defenses in a recent Patchstack case study. Across five hosting and WAF configurations, only 12.2% of WordPress-specific attacks were stopped before reaching the application. Patchstack’s application-aware layer blocked all 11 test exploits. The sample is small and vendor-run, but it quantifies a risk for teams relying only on generic WAF or malware tools for WordPress protection.
Executive snapshot
Patchstack tested five hosting security setups against 11 WordPress-specific vulnerabilities, recording whether network or server controls stopped each exploit before it reached the application. In aggregate, perimeter defenses blocked 12.2% of exploits, while 87.8% reached WordPress. Patchstack’s WordPress layer then blocked 100% (11 of 11) in the test environment.
- Cloudflare WAF: 4 of 11 exploits blocked in the tested configuration
- Monarx: 0 of 11
- Imunify: 0 of 11
- ConfigServer Firewall: 0 of 11
- Across hosts: two blocked 0 of 11, one blocked 1 of 11, one blocked 2 of 11, one blocked 4 of 11
The study notes that plugin and theme vulnerabilities are often weaponized within hours of public proof-of-concept release, reducing response time for site owners.
Why it matters for marketers
If your revenue site runs on WordPress and relies only on host-layer WAF or malware tools, most plugin and theme exploits are likely unmitigated at the perimeter. The result is higher risk of downtime, defacement, and data loss that can harm conversions, paid campaigns, and SEO.
Method and sources
What was measured: Block rates for 11 WordPress-specific vulnerabilities across five hosting stacks, distinguishing blocks at the network or server layer versus the application-level WordPress layer. Identical WordPress builds served as honeypots, and a controlled toolkit executed the same exploit sequence on each site. Blocks were verified automatically and manually, and the responsible layer was recorded.
By whom and when: Patchstack conducted and published the case study. Search Engine Journal summarized the findings in August 2025. Primary source: Read the results of the case study by Patchstack here.
Sample and configuration: Five distinct stacks - (A) host + Cloudflare WAF, (B) host + firewall + Monarx, (C) host + firewall + Imunify, (D) host + ConfigServer Firewall, (E) host + firewall. Patchstack was installed on all sites to observe what passed the perimeter.
Findings
Overall performance: Perimeter defenses blocked 12.2% of WordPress-specific exploits; 87.8% reached the application. Patchstack blocked all 11 exploits that reached it in this setup.
Solution-level outcomes:
- Cloudflare WAF: 4 of 11 blocked in the tested configuration
- Monarx: 0 of 11
- Imunify: 0 of 11
- ConfigServer Firewall: 0 of 11
- An unnamed host firewall blocked 1 or 2 of 11
Attack class differences: Generic WAFs and server firewalls fared better on broad patterns like SQL injection or XSS, but struggled with plugin or theme-specific chains such as privilege escalation or authentication bypass that do not match generic signatures. These often require targeted, application-aware rules or virtual patches.
Response timing: Exploitation often begins within hours of proof-of-concept publication, compressing the window in which generic defenses or manual patching can prevent compromise.
Interpretation and implications
- Perimeter controls alone are insufficient for WordPress risk - the 87.8% bypass rate suggests many plugin and theme exploit paths evade broad signatures.
- Application-aware virtual patching can reduce exposure between disclosure and vendor update - in this test, Patchstack blocked 11 of 11 at the WordPress layer.
- Time-to-mitigation should be measured in hours - with fast-moving exploitation, update SLAs and app-level mitigations need accelerated operations.
- Layered defense still adds value - tools like Cloudflare can filter commodity traffic and broad attack classes, lowering baseline risk and resource load, but should not be the primary control for WordPress plugin or theme flaws.
Limitations and caveats
- Small sample - five stacks and 11 vulnerabilities - with vendor conflict of interest. Results are directional, not market benchmarks.
- Configuration details are not fully disclosed - plan tiers, managed rulesets, and tuning can materially affect WAF outcomes.
- Vulnerability mix is not enumerated - results may vary with other plugin or theme flaws.
- No assessment of false positives, performance overhead, or operational impact.
Data appendix
- Test matrix: five hosting stacks, identical WordPress builds, 11 WordPress-specific vulnerabilities, automated plus manual verification of block source.
- Aggregate outcomes: perimeter defenses blocked 12.2% of exploits; 87.8% bypassed to the application; application-level layer blocked 11 of 11 after bypass.
- Per-solution notes: Cloudflare WAF 4 of 11, Monarx 0 of 11, Imunify 0 of 11, ConfigServer Firewall 0 of 11, one unnamed host firewall 1 or 2 of 11.
Sources
- Read the results of the case study by Patchstack here
- Search Engine Journal - Common Hosting Defenses Ineffective Against WordPress Threats (summary of the Patchstack case study, Aug 2025)



.svg)