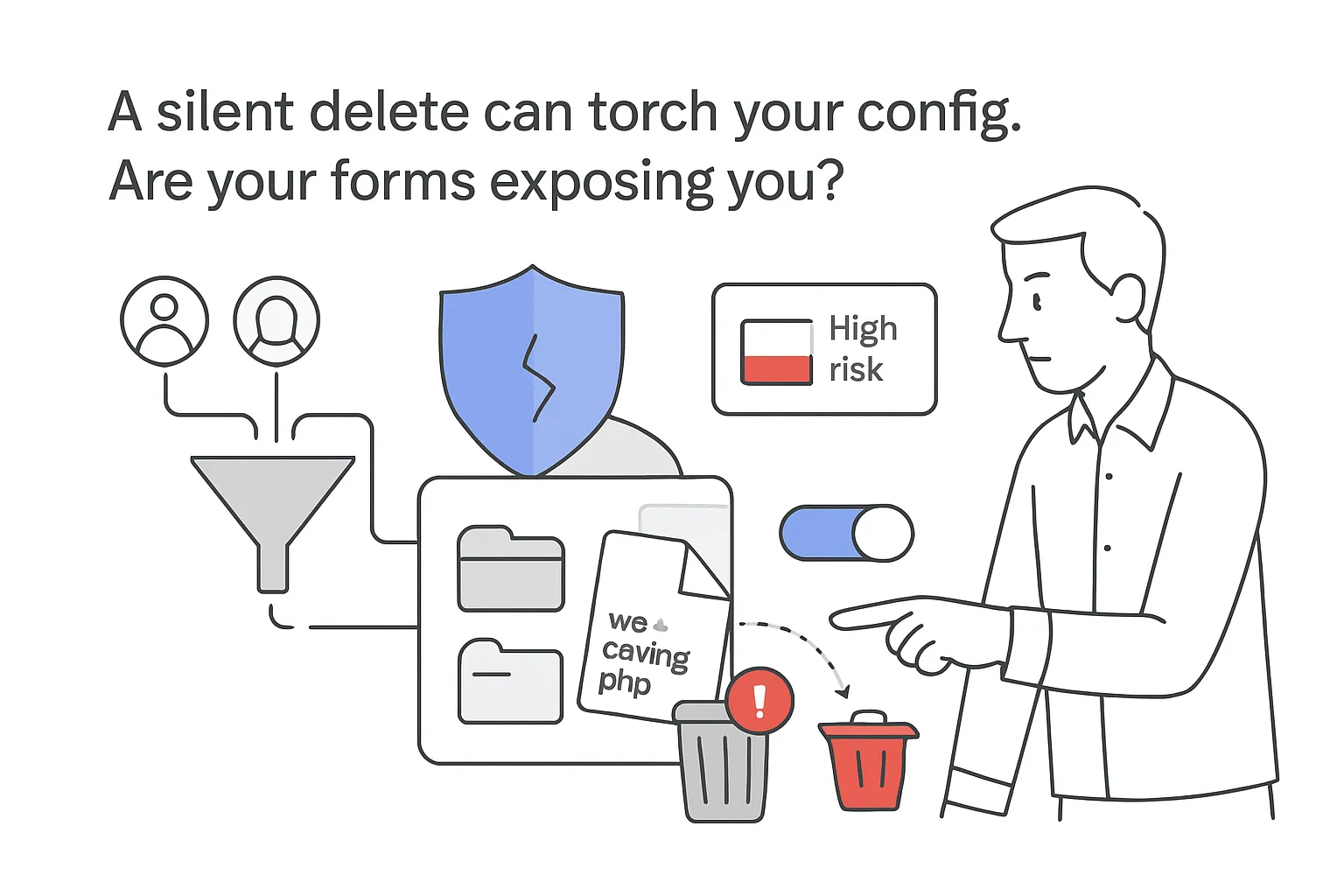
Wordfence has issued a high-severity advisory for Redirection for Contact Form 7, a WordPress add-on with more than 300,000 active installations. The flaw allows unauthenticated arbitrary file deletion and is rated CVSS 8.8. All versions up to and including 3.2.4 are affected.

Key details
- Affected plugin: Redirection for Contact Form 7 - slug wpcf7-redirect. Official WordPress.org plugin listing.
- Advisory source: Wordfence Threat Intelligence, which explains the issue in detail.
- Vulnerability: Unauthenticated arbitrary file deletion due to insufficient file path validation in the delete_associated_files function.
- Severity: High - CVSS 8.8, per Wordfence.
- Affected versions: All versions up to and including 3.2.4.
- Install base: More than 300,000 active installations, per the WordPress.org directory.
- Impact: Deleting a critical file such as wp-config.php can enable remote code execution, according to Wordfence.
Background
Redirection for Contact Form 7 extends the core Contact Form 7 plugin with redirect, database storage, notification, and spam-blocking options. Wordfence attributes the flaw to insufficient validation in a file deletion routine that lets attackers remove arbitrary files without authentication. Removing wp-config.php can open a path to remote code execution.



.svg)