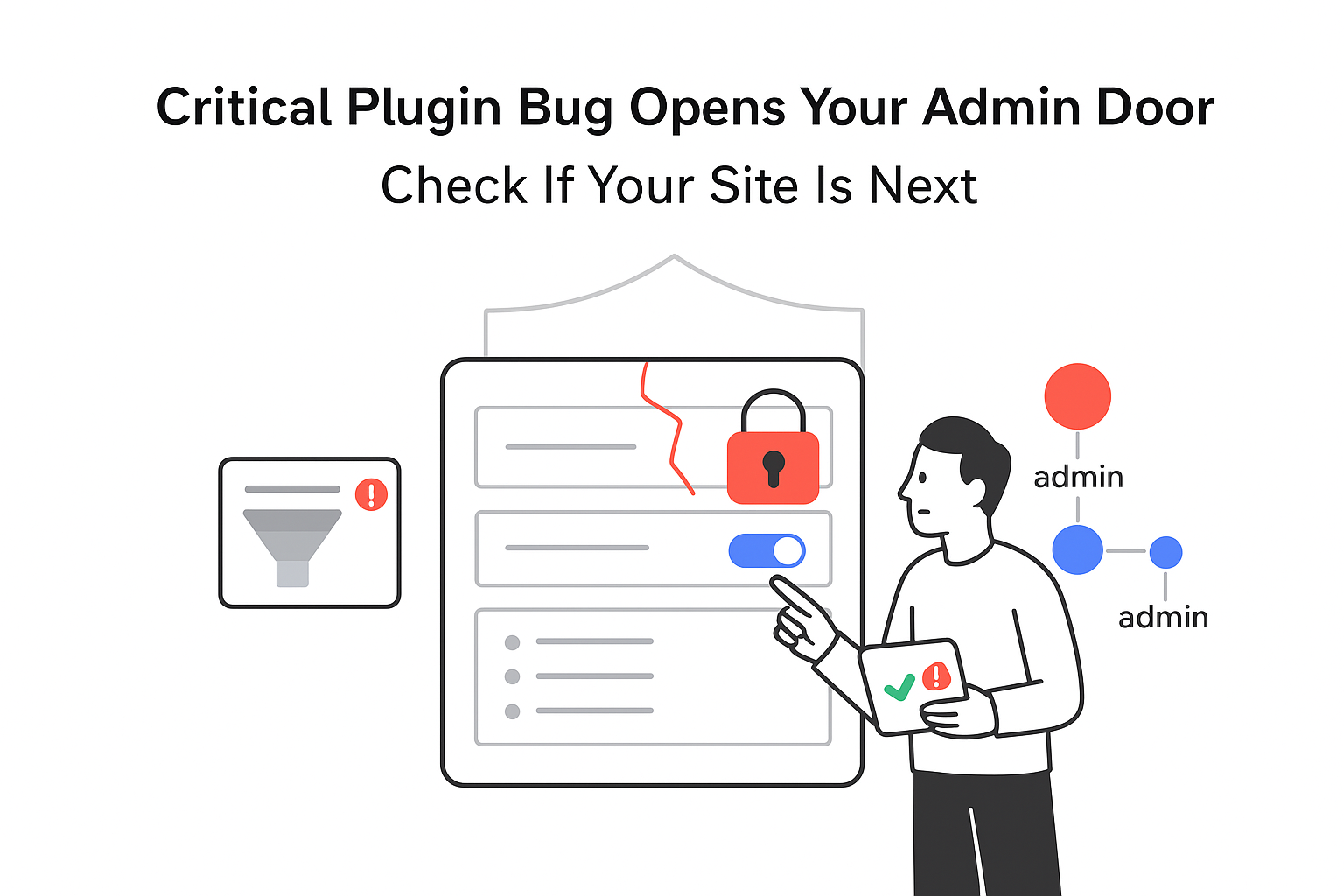
Security firm Wordfence has disclosed a high-severity vulnerability in the Advanced Custom Fields: Extended (ACF Extended) WordPress plugin. The flaw affects up to 100,000 installations and allows unauthenticated attackers to gain administrator access to targeted sites.

Key details: WordPress Advanced Custom Fields Extended plugin vulnerability
The Advanced Custom Fields: Extended plugin is an add-on for Advanced Custom Fields Pro and has more than 100,000 active installations, according to its listing on WordPress.org. Wordfence rates the vulnerability at 9.8 (critical) in its published Wordfence advisory.
- Affected plugin: Advanced Custom Fields: Extended (free Basic edition)
- Vulnerability type: unauthenticated privilege escalation via user registration
- Impacted versions: all releases up to and including 0.9.2.1
- Patched version: 0.9.2.2, which adds stricter validation for front-end forms and role selection
- Exposure: sites using front-end forms that map a custom field directly to the WordPress "role" field
According to Wordfence, the plugin's insert_user function does not properly restrict which roles can be assigned during registration. When a front-end form exposes a role field, attackers can submit a request that sets the role to administrator for a new account. The plugin passes this role value directly to WordPress without validating it against the field's configured choices.
Successful exploitation gives attackers administrator-level privileges on the affected WordPress site. With administrator access, attackers can install or modify plugins and themes, inject malicious code, create persistent backdoor accounts, steal or manipulate stored data, and change site configuration settings.
Background context
The Advanced Custom Fields: Extended plugin works with Advanced Custom Fields Pro to add tools for forms and content types. Developers use it to manage front-end forms, create options pages, define custom post types, and modify the WordPress admin interface. These capabilities make the plugin common on sites with advanced content workflows and user-facing submission forms.
The vulnerability applies when a site uses an ACF Extended front-end form that maps a field to the WordPress role. If that configuration exists, unauthenticated visitors can send crafted requests that change the role value to administrator. Wordfence reports that its firewall has already blocked real-world attempts targeting this weakness.
Version 0.9.2.2 of ACF Extended Basic introduces multiple validation changes for forms, according to the official plugin changelog. The update enforces front-end field validation against each field's configured choices and adds extra security checks for user role selection. New hooks also allow developers to validate or bypass validation of individual fields on form submission.
Source citations
Key technical details and patch information are documented in official security and plugin release materials.
- Wordfence advisory describing the unauthenticated privilege escalation vulnerability
- Official plugin changelog detailing fixes released in version 0.9.2.2
- Additional reporting by Search Engine Journal on the ACF Extended vulnerability and exploitation activity




.svg)