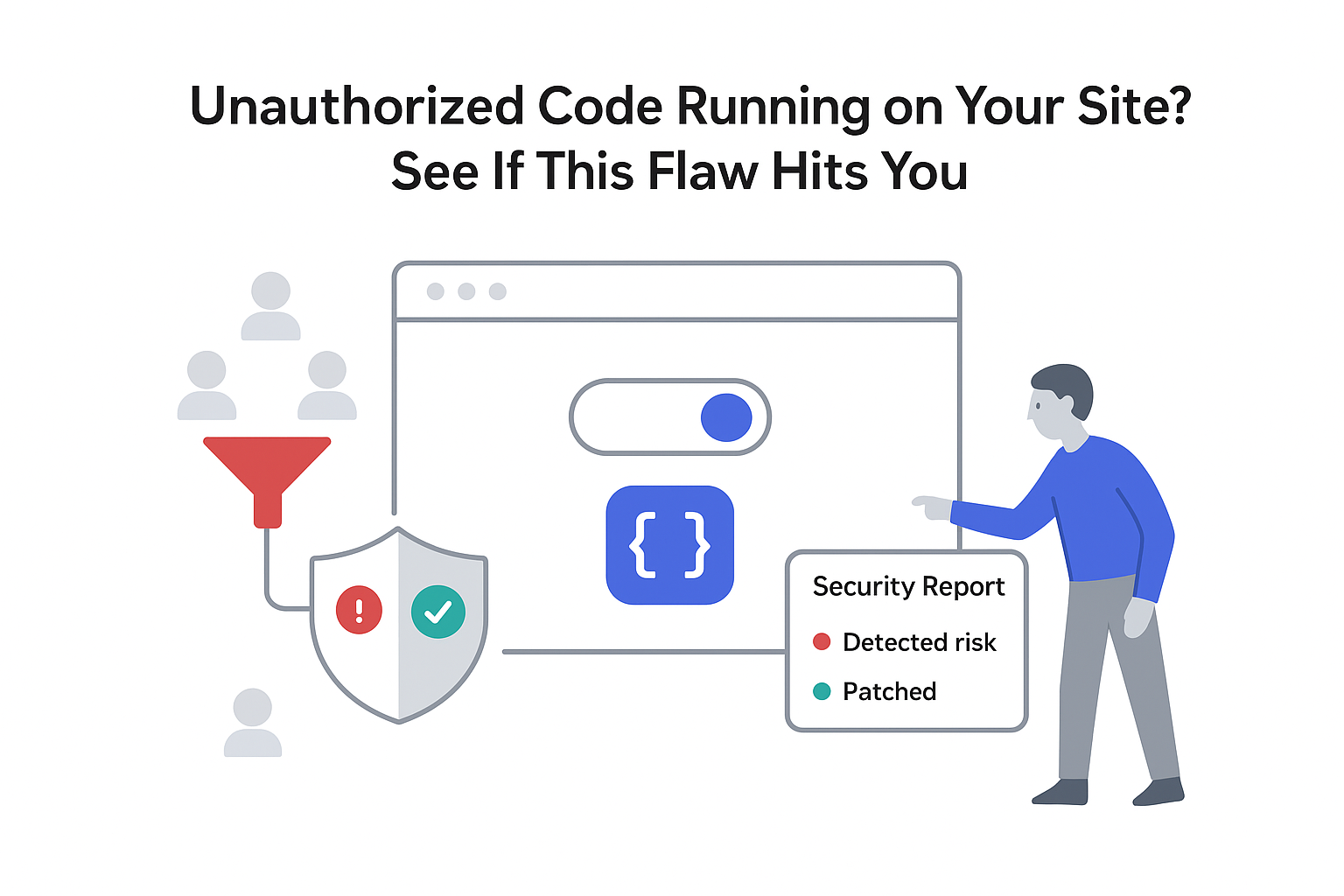
A high severity security flaw has been disclosed in the BuddyPress WordPress plugin, widely used on community and membership websites. The issue allows unauthenticated arbitrary shortcode execution on vulnerable sites and has been fixed in a recent plugin release.

BuddyPress WordPress vulnerability details
BuddyPress is installed on more than 100,000 WordPress websites, based on the plugin's official statistics. Wordfence Threat Intelligence has documented a vulnerability affecting all BuddyPress versions up to and including 14.3.3.
The flaw allows unauthenticated visitors to trigger arbitrary WordPress shortcodes through a BuddyPress action exposed on affected sites. It carries a CVSS score of 7.3 and is classified as high severity in the Wordfence advisory.
- Affected product: BuddyPress plugin for WordPress.
- Affected versions: all releases up to and including 14.3.3.
- Vulnerability type: unauthenticated arbitrary shortcode execution.
- Authentication required: none to trigger the affected shortcode functionality.
- Technical cause: missing validation of a user-supplied value before execution via the WordPress
do_shortcodefunction. - Installation base: more than 100,000 active sites as reported for the plugin.
- Configuration dependencies: the vulnerability does not rely on special server settings or optional configurations.
Background on the BuddyPress plugin
BuddyPress extends WordPress with social networking features, including user profiles, activity streams, private messaging, and groups. It is commonly used on membership and community sites that embed interactive user functionality within WordPress.
Public vulnerability tracking in 2025 recorded one BuddyPress security issue before this latest disclosure. That earlier issue carried a score of 5.3 on a 1-10 scale and was categorized as medium severity.
Official advisories and patch status
In its advisory, Wordfence described the BuddyPress flaw as an arbitrary shortcode execution vulnerability affecting versions through 14.3.3. The notice appears in the Wordfence Threat Intelligence database of WordPress plugin issues.
The advisory explains that an action in BuddyPress fails to validate a user-controlled value before calling WordPress's do_shortcode function. This behavior lets unauthenticated users trigger arbitrary shortcode execution on affected sites.
The issue has been addressed in BuddyPress version 14.3.4, which includes a fix for the shortcode validation problem. Details of the vulnerability and remediation steps are described in the Wordfence advisory.




.svg)