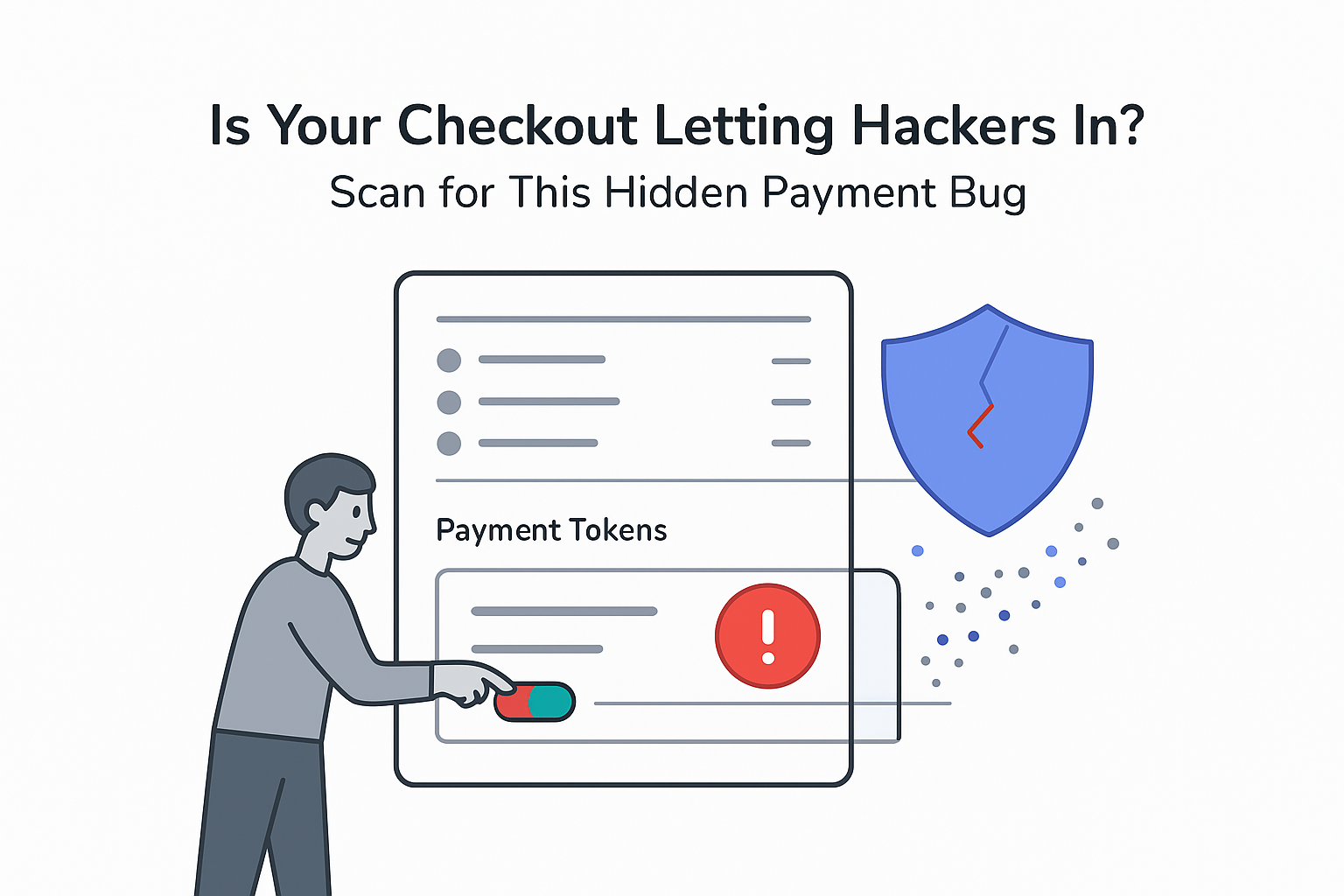
Wordfence has disclosed a vulnerability in the WooCommerce Square plugin that may affect up to 80,000 WordPress sites. The flaw allows unauthenticated attackers to access stored payment tokens and potentially trigger fraudulent charges through connected Square accounts, according to the company's threat intelligence team.
WooCommerce WordPress Plugin Exploit Enables Fraudulent Charges
The WooCommerce Square plugin connects WooCommerce stores with Square point-of-sale services and payment processing. It supports Apple Pay, Google Pay, WooCommerce Pre-Orders, and WooCommerce Subscriptions for recurring and scheduled payments.

According to Wordfence, plugin versions up to and including 5.1.1 contain an Insecure Direct Object Reference (IDOR) vulnerability. The issue appears in the get_token_by_id function, which fails to validate a user-controlled key parameter. This weakness allows unauthenticated attackers to request arbitrary Square credit-card-on-file identifiers linked to customer accounts.
Key details reported by Wordfence include:
- Unauthenticated access to the vulnerable function via public site endpoints.
- Exposure of Square "ccof" values, which represent stored credit cards on file.
- Use of exposed "ccof" values to initiate fraudulent charges through the merchant's Square setup.
- Impact across an estimated 80,000 active WooCommerce Square installations.
Exploitation of the flaw does not require any authentication or user role on the targeted WordPress site. Wordfence characterizes the bug as unauthenticated and remotely exploitable against vulnerable installations.
Background Context
The WooCommerce Square plugin synchronizes product inventory between WooCommerce and Square while handling both card-present and online payments. Merchants can accept payments through web checkouts and compatible wallets and manage stock across both platforms from a single catalog.
OWASP defines IDOR as an access control weakness where exposed identifiers in requests are not properly checked, allowing attackers to access data or actions belonging to other users.
Wordfence reports that the get_token_by_id function did not verify whether the requesting party owned the referenced token. The company states that the flaw "makes it possible for unauthenticated attackers to expose arbitrary Square 'ccof' values" and that attackers can then "potentially make fraudulent charges on the target site" using those values.
Patches, Severity Score, and Official Advisories
Wordfence lists multiple patched WooCommerce Square releases that address the vulnerability across different version branches. The following versions are reported as fixed:
- 4.2.3
- 4.3.2
- 4.4.2
- 4.5.2
- 4.6.4
- 4.7.4
- 4.8.8
- 4.9.9
- 5.0.1
- 5.1.2
According to Wordfence, the vulnerability carries a Common Vulnerability Scoring System (CVSS) score of 7.5, placing it in the High severity range but below the threshold for a Critical classification.
A detailed Wordfence advisory documents the issue and lists the patched versions. OWASP's guidance on Insecure Direct Object Reference offers general best practices for preventing similar access control weaknesses in web applications.




.svg)