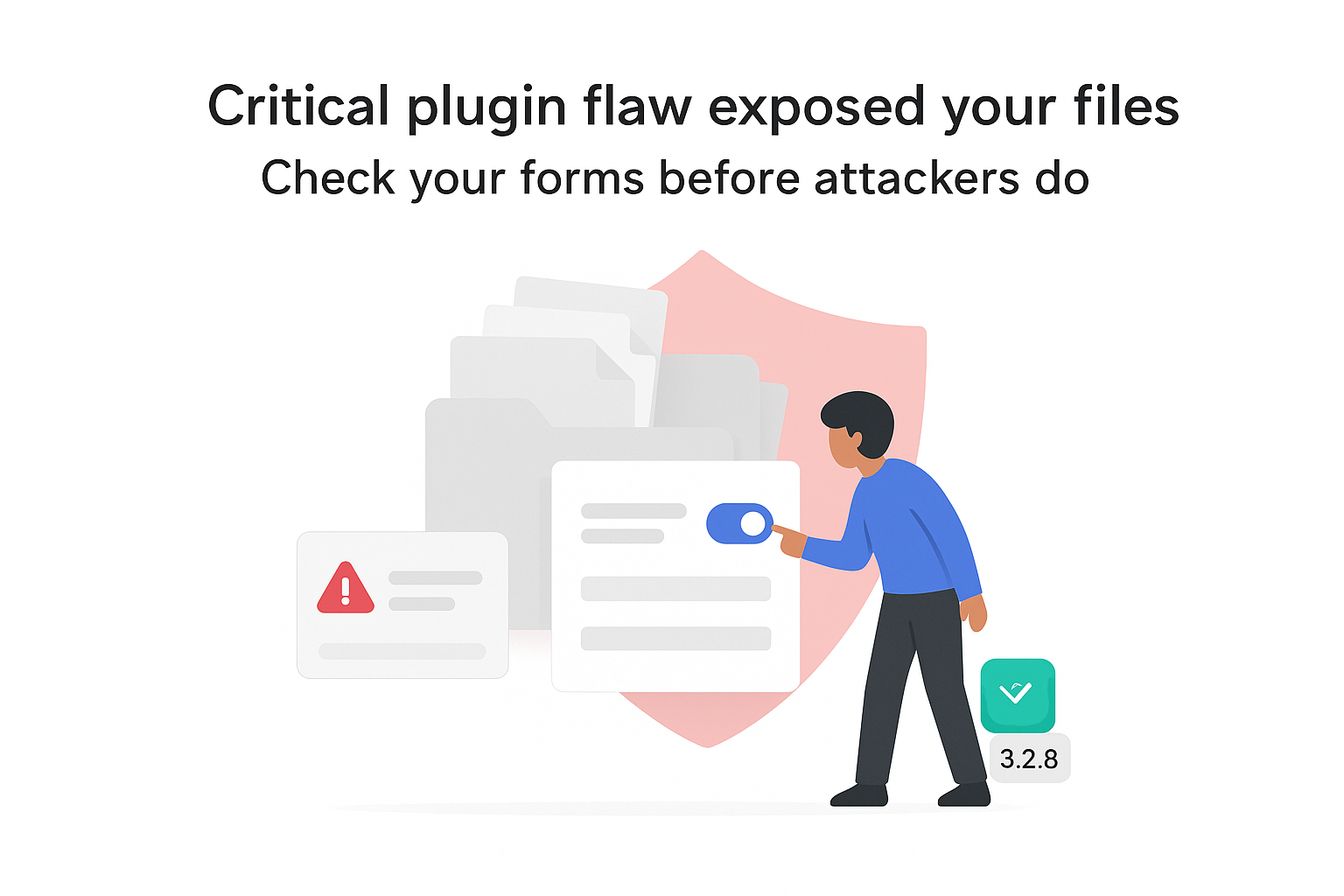
Security firm Wordfence has disclosed a high severity vulnerability in the Redirection for Contact Form 7 WordPress plugin. The flaw affects all versions up to and including 3.2.7 and could allow attackers to manipulate files on servers running the plugin. Developed by ThemeIsle, the add-on extends Contact Form 7's form handling by managing redirects and storing submissions.

Key details
In its advisory, Wordfence classifies the issue as an unauthenticated arbitrary file copy vulnerability. The weakness stems from missing file type validation in the plugin function move_file_to_upload. Because the flaw can be exploited without a user account, any unauthenticated visitor could attempt to abuse it on a vulnerable site.
Wordfence assigns the vulnerability a CVSS score of 8.1 out of 10, rated High. The bug allows attackers to copy arbitrary files on the site server. In some environments, it can also be leveraged for remote file upload.
According to the advisory, remote file upload becomes possible when the PHP setting allow_url_fopen is enabled on the server. With that directive on, the lack of file validation in the plugin can permit files to be uploaded from external locations.
- Plugin: Redirection for Contact Form 7, developed by ThemeIsle.
- Function: Redirects users after form submission and can store submissions in a database.
- Active installations: More than 300,000 sites, according to the WordPress.org plugin directory.
- Vulnerability type: Unauthenticated arbitrary file copy and, in some configurations, remote file upload.
- Fixed version: Wordfence notes that release 3.2.8 of the plugin addresses the vulnerability.
Background context
Redirection for Contact Form 7 is an add-on for the separate Contact Form 7 plugin for WordPress. It lets site owners define custom pages where visitors land after submitting a form, record form data in a database, and trigger additional actions based on submissions.
The plugin is distributed through the official WordPress.org listing for Redirection for Contact Form 7 under the slug wpcf7-redirect. ThemeIsle maintains the software and publishes release notes and updates on that platform. Contact Form 7 itself is maintained separately by developer Takayuki Miyoshi and is available via its own WordPress.org plugin listing.
PHP's allow_url_fopen directive controls whether functions such as fopen can access remote files using URLs. PHP documentation notes that the default value is often "On", but server administrators can change it. Wordfence reports that in this case, remote file upload associated with the vulnerability depends on that setting being enabled.
Source citations
Details of the vulnerability, affected versions, and the fix are documented in public advisories and official plugin resources:




.svg)